The Systems Security Lab (SySec) @ LSU is a research lab dedicated to exploring and building cybersecurity solutions for IoT and the Mobile platforms. Particularly, we leverage methodologies such as binary instrumentation, software reverse engineering, memory forensics, and machine learning to address security, privacy, and forensics problems in the following focus areas:
Digital Forensics & Cybercrime Investigations
Over the last decade, userland memory forensics techniques and algorithms have gained popularity among practitioners, as they have proven to be useful in real forensics and cybercrime investigations. These techniques analyze and recover objects and artifacts from process memory space that are of critical importance in investigations. This research presents app-agnostic userland memory analysis techniques that targets the new Android Runtime (ART). Leveraging its latest memory allocation algorithms, called region-based memory management, we develop sets of tools for recovering vital runtime data structures for applications by enumerating and reconstructing allocated objects from a process memory image. In addition, our set of tools and semantic analysis algorithms can aid investigators establish concrete evidence by identifying the provenance and relationships between in-memory objects in a process memory image. This project is funded under the NSF SatC CRII grant.
Malware Analysis and Threat Assessment
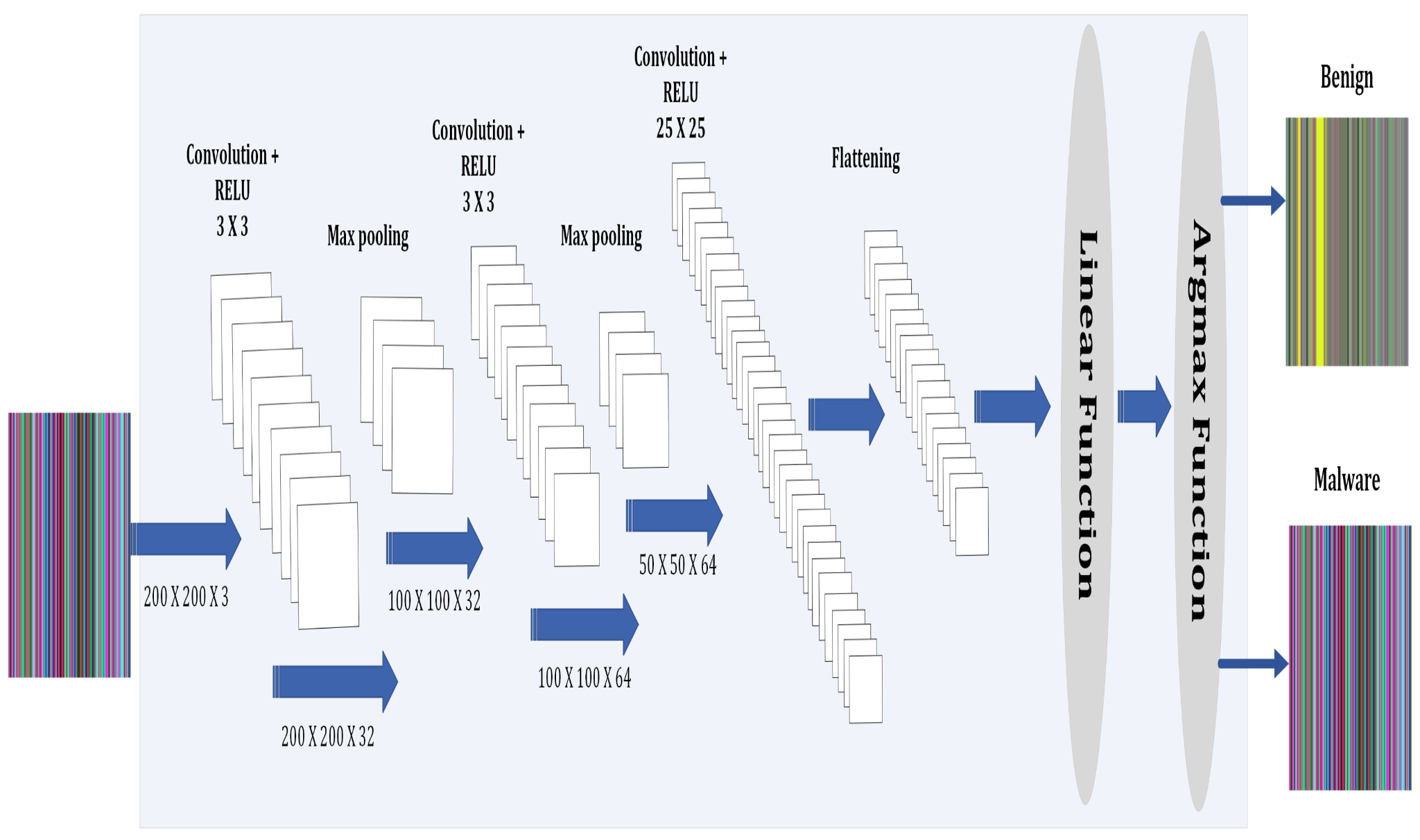
Mobile malware’s alarming sophistication and pervasiveness have continued to draw the attention of many cybersecurity researchers. Particularly on the Android platform, malware trojans designed to steal user PIIs, crypto miners, ransomware, and on-device fraud continue to infiltrate the primary Google store market and other secondary markets. While much effort has been put in place by the research community and industry to curb this menace since 2012, malware authors have consistently found ways to circumvent the existing detection and prevention mechanisms. Largely this remains so because of the restrictiveness of the feature set used in building the current classification models. Thus, the overarching objective of this project is to bridge the gap between static and dynamic analysis by exploring the use of in-memory artifacts generated from the concrete execution of Android apps for effective malware classification. This project is funded under the NSF SatC CRII grant.
System Defenses - IDS, Access Control, etc
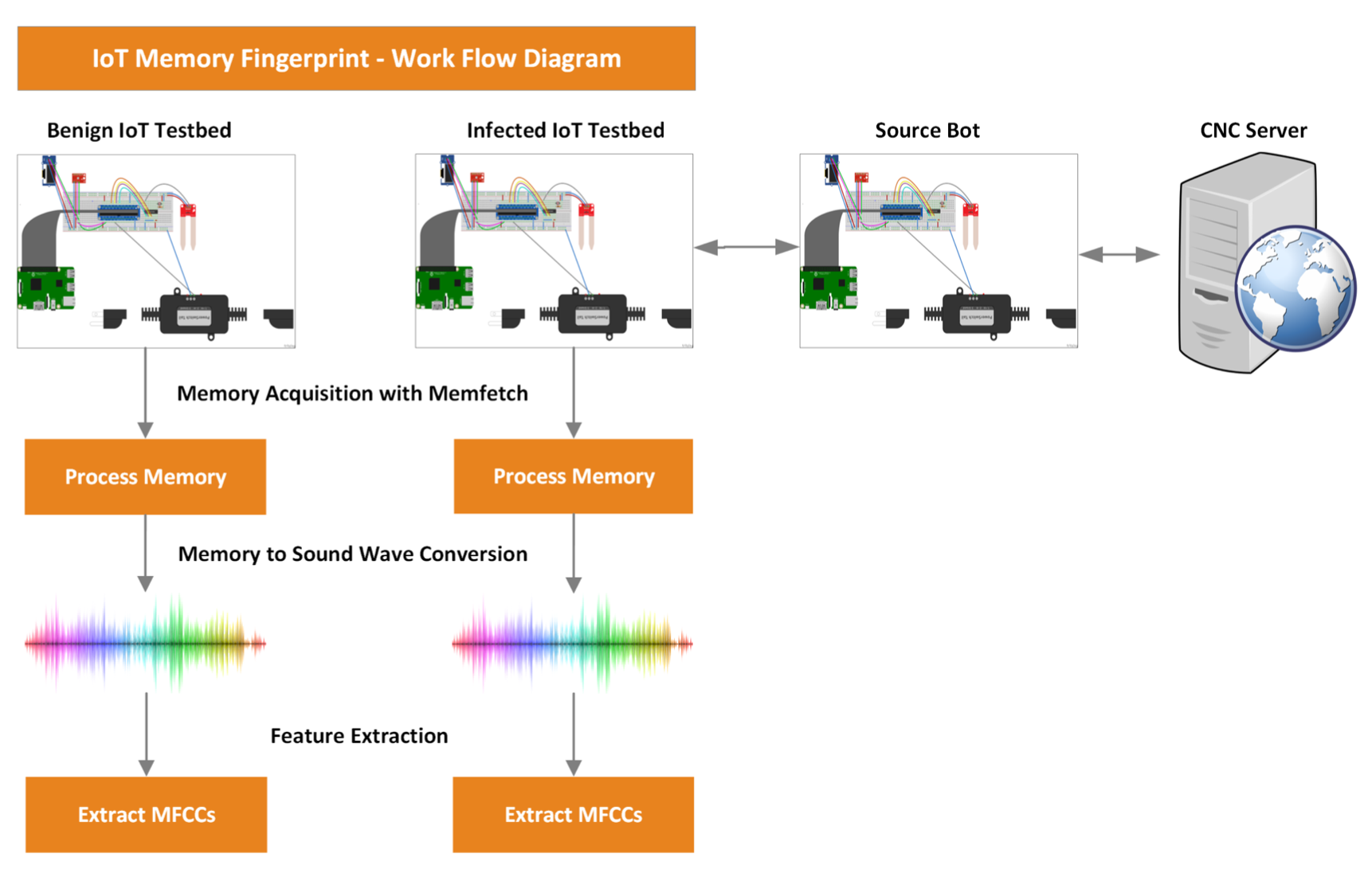
The increasing sophistication in computing capability and sensing technologies have continued to drive the design, development, and growth of the smart technologies commonly known as the IoTs. Nonetheless, the rise and spread of malware in this ecosystem is a pressing societal concern that requires immediate attention. This project propose a novel technique for fingerprinting IoT devices by converting their dynamic memory traces into sound wave signals using a lossless transformation function from which a unique set of determinable features called Mel Frequency Cepstral Coefficients (MFCCs) are extracted. The overarching objective of this research is to explore offline the effectiveness of using features from memory-encoded sound wave signals for fingerprinting and detecting abnormal changes in IoT devices, which potentially can provide an excellent technique for an on-device Host-Based Intrusion Detection System. This project is funded under the NCAE Research Innovation grant.
Privacy Modeling and Enforcement
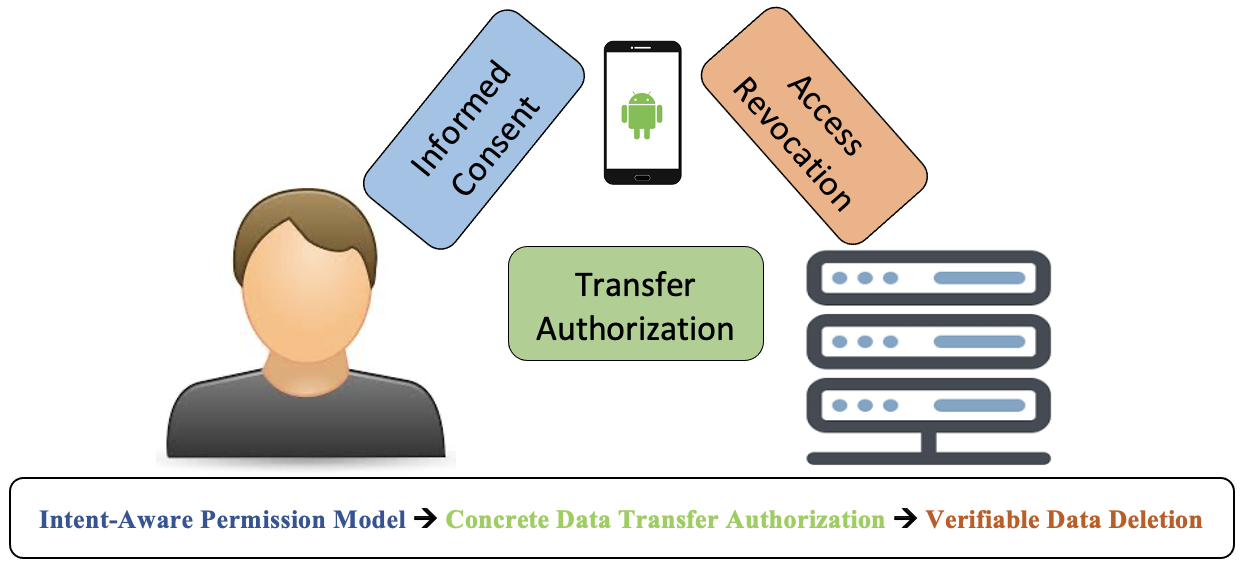
As data privacy continues to be a crucial human-right concern as recognized by the UN, regulatory agencies have demanded developers obtain user permission before accessing user-sensitive data. Mainly through the use of privacy policies statements, developers fulfill their legal requirements to keep users abreast of the re quests for their data. In addition, platforms such as Android enforces explicit permission request using the permission model. Nonetheless, recent research has shown that service providers hardly make full disclosure when requesting data in these statements. Neither is the current permission model designed to provide adequate informed consent. Often users have no clear understanding of the reason and scope of usage of the data request. This research proposes an unambiguous, informed consent and access revocation process that provides developers with a standardized method for declaring Intent as well verifiable data deletion mechanism.
The Team
Graduate Students

Ramyapandian Vijayakathan (TU)

Tanzila Tabassum

Karley Waguespack - Co-supervise with Golden G. Richard III

Mst E. Kathun

Sideeq Bello

Babangida Bappah
Undergraduate Students

Olame Muliri

Nicholas Tenat

Nicholas Caplette

Arabelle Betzwieser
Former Students - Doctorate

Bassam Zahran (Graduate - TU)

Sneha Sudhakaran (Graduate - LSU, Co-Supervised with Golden G. Richard III)

Nicholas Phillips (Graduate - TU)
Former Students - Masters
Donald Lafleur
Melissa Stitts
Ali Almaliki
Former Students - Undergraduates
Kordell Hutchin - Capital One
Zakiya Talley - Dell Corporations
Crystal Omari - MITRE
Elizabeth Miller - CAI
Oluwasetemi Owoeye
Anjita Bhandari
Makayla St Cyr
Angela Gurfolino
Alexandra Tambaoan
Ambe Tangwan-Afor
Megan Wysocki
Ma. Bettina Bienvenida
Sabina Aguon
